In the ever-evolving world of OSINT (Open Source Intelligence), automation is now essential — especially when investigations span emails, domains, usernames, phone numbers, and more.
Today I’m taking a look at Sherlockeye, a web-based AI-powered platform designed to speed up reconnaissance and threat analysis activities.
Here’s my take based on real usage and testing.
🧪 First Impressions & Interface
Sherlockeye’s homepage is sleek and dark-themed — a nice touch for late-night analysts (we’ve all been there).
At the core is a single input field where you can choose your input type:
- Auto (smart detection)
- Bucket
- CNPJ / CPF (Brazilian identifiers, especially useful for LATAM investigations)
- Domain
- IP
- Phone
- Username
Switching between modes is smooth, and the UI is intuitive for both beginners and experienced OSINT researchers.
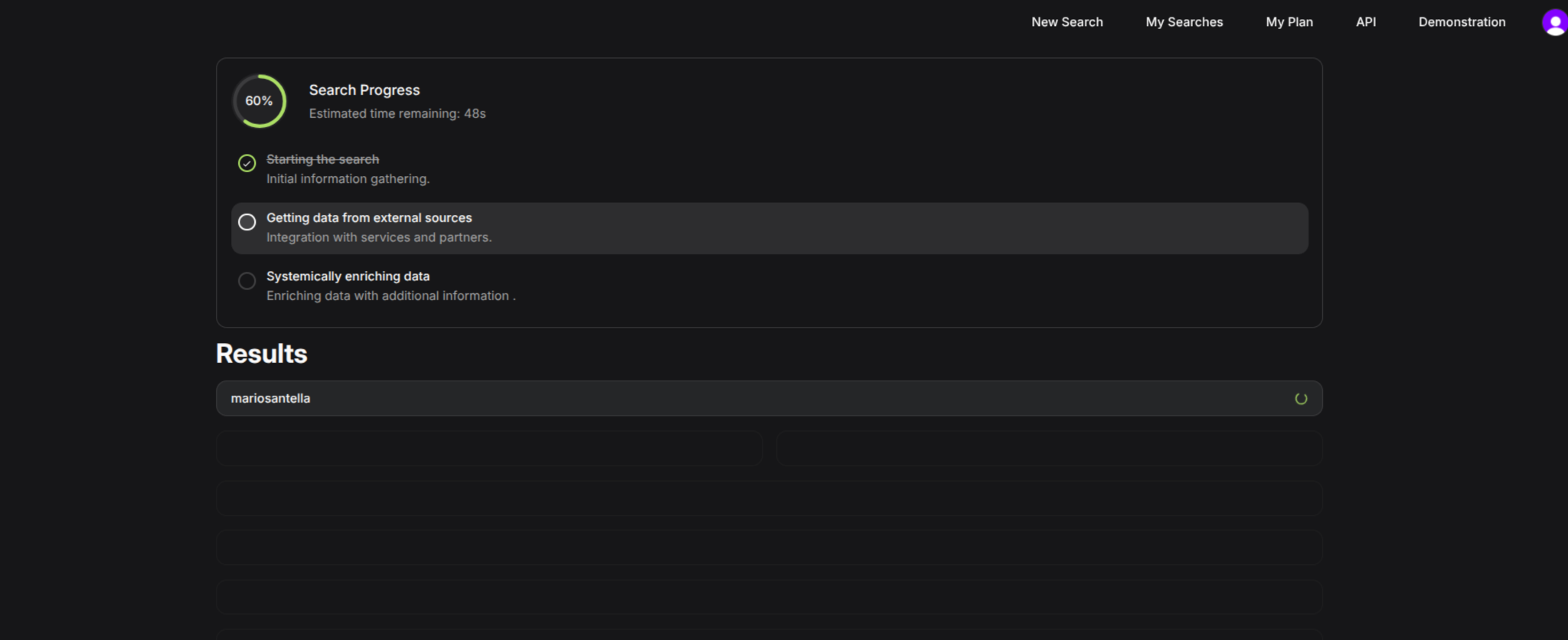
🔄 Enrichment & Search Progress
Once you start a search (in this case I used my old nickname mariosantella — yes, that one, the infamous international hacker 😅), Sherlockeye displays a clear progress indicator:
- Initial data gathering
- Integration with external sources
- Systemic enrichment with AI
I genuinely appreciate this level of transparency. It shows that the data isn’t just pulled from static lists, but actively enriched in real time.
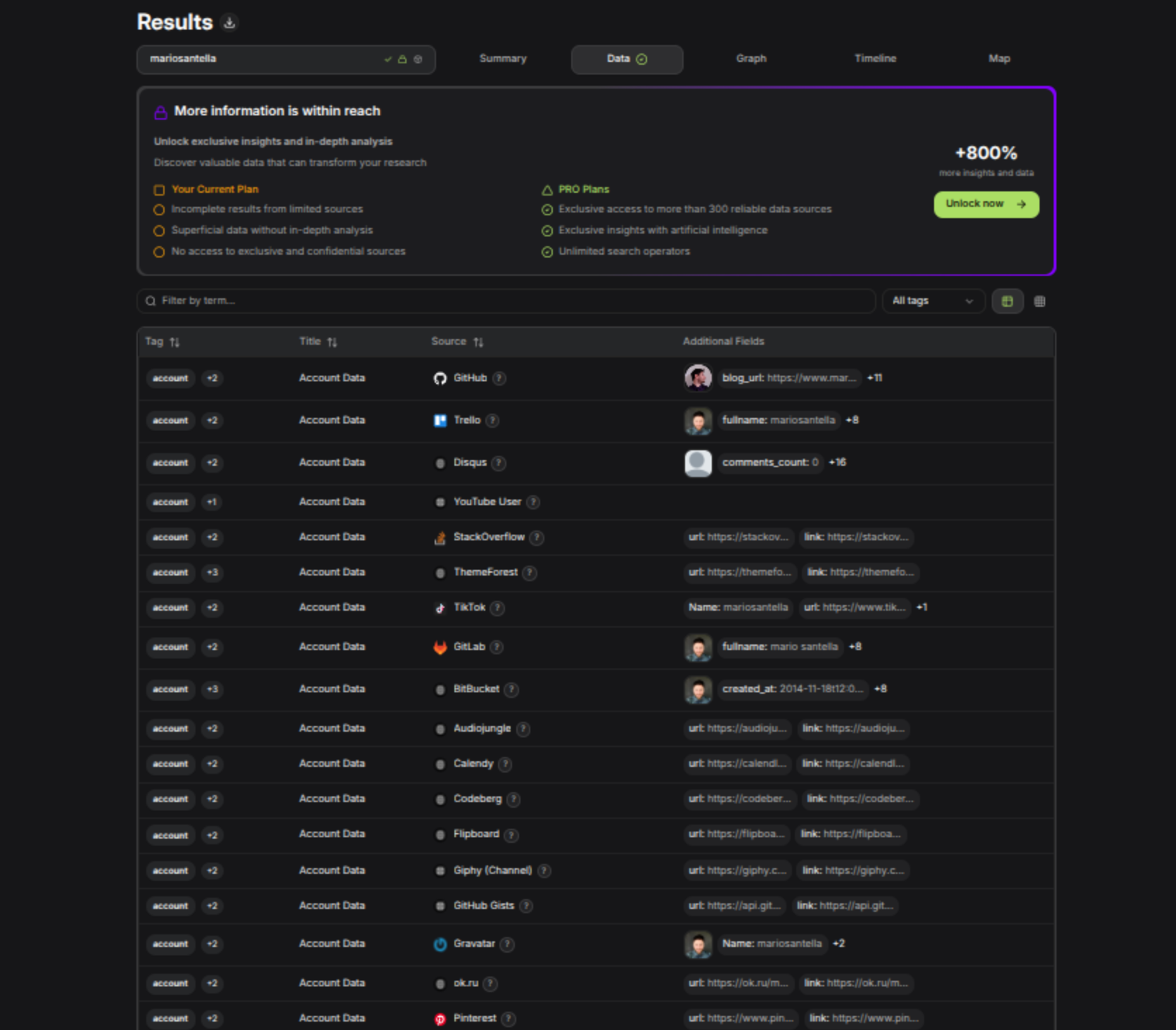
📊 Results: Structured and Rich
This is where Sherlockeye shines.
Results are grouped by account type (GitHub, Trello, StackOverflow, TikTok, etc.), and each result includes:
- Blog/profile URLs
- Full name
- Creation date
- Comment count
- Other contextual metadata
Each result is tagged, hyperlinked, and sortable — with filtering options to refine your view. This is extremely helpful for focused investigations.
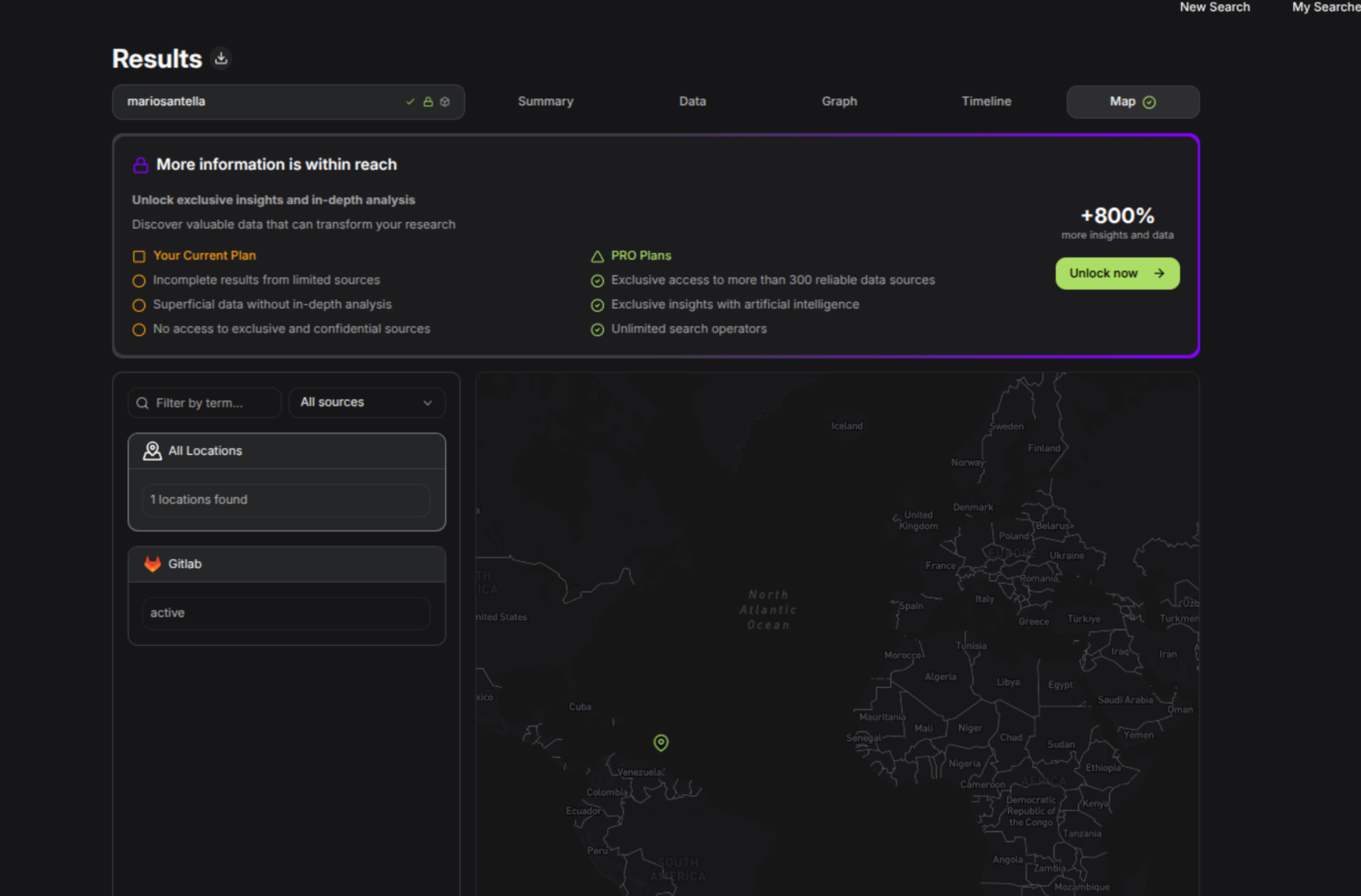
🌍 Geolocation & Map Tab
Another useful feature is the Map view. When Sherlockeye extracts location hints from sources (as with GitLab in my test), it places them on an interactive map.
A quick note here: you’ll get the most out of this feature when starting from a Gmail or Google-related email address — these tend to be far more fruitful than simple usernames.
💰 Plans & Limitations
Sherlockeye claims to tap into 300+ reliable data sources, but as expected, the free plan is intentionally limited. You’ll get:
- Partial results from a smaller subset of sources
- Shallow data without deep enrichment
- No access to exclusive or confidential data
And that’s totally fair.
The tool works well, the interface is clean, and if you want full power — it makes sense to go PRO. It’s a reasonable, sustainable model for a serious OSINT platform.
⚖️ Verdict: Is It Worth It?
✅ Pros:
- Clean and smooth interface
- Solid enrichment logic (AI + external sources)
- Support for many input types (email, phone, domain, username, etc.)
- Advanced visualizations: timeline, graph, map
- API available for automation or integration
- Beginner-friendly while still powerful
❌ Cons:
- Free plan is limited — best for exploration or testing
👨💻 Final Thoughts
Sherlockeye is a promising OSINT tool — especially for quickly spinning up reconnaissance across multiple entity types.
and significantly lowers the entry barrier for professional digital investigations.
If you work in cybersecurity, digital forensics, or are simply curious about what hides behind a name or account — Sherlockeye is worth a try.
Just be ready to upgrade if you want to unlock its full potential.
