Let’s talk about security. Everyone’s obsessed with complex zero-day exploits and APTs. But in the real world, the most damaging breaches often come from the dumbest, most obvious holes you can imagine. We found one. It was a doozy.
The Scenario: A Ticking Time Bomb
Our client? A sharp web agency that manages a portal handling state-level bureaucracy. Think sensitive personal data, the kind of stuff that makes banks nervous. As the platform grew, so did its digital footprint. And so did the target on its back.
The challenge was simple on the surface: Block malicious traffic.
The reality was a nightmare.
They couldn’t just drop a firewall and call it a day. Why?
Because a huge chunk of their legitimate users-bank employees, financial advisors, you name it-work remotely. They use VPNs, corporate proxies, all sorts of services that give them a “Low Score” or “unclean” IP address.
Blocking these IPs meant blocking their own users. A blanket ban was business suicide. So they were stuck, letting everyone in, hoping their password policies were enough. (they weren’t.)
Phase 1: Strategic Intelligence, Not Blanket Bans
Here’s the core of the problem, stripped down: An IP from a VPN accessing a public page is normal business. The same IP using a valid admin password to get into /admin.php is a red flag.
The risk isn’t the IP itself, but the context of the access.
So, we stopped trying to boil the ocean. We focused on the one place that mattered: the admin login. Our proposal was to apply a zero-trust policy *only* where it was critical.
We integrated the Criminal IP Enterprise API directly into the admin authentication flow. This wasn’t about blocking everyone with a bad IP; it was about making an intelligent decision for privileged access.
Here’s how Criminal IP became the key: it provides a complete risk profile for each IP.
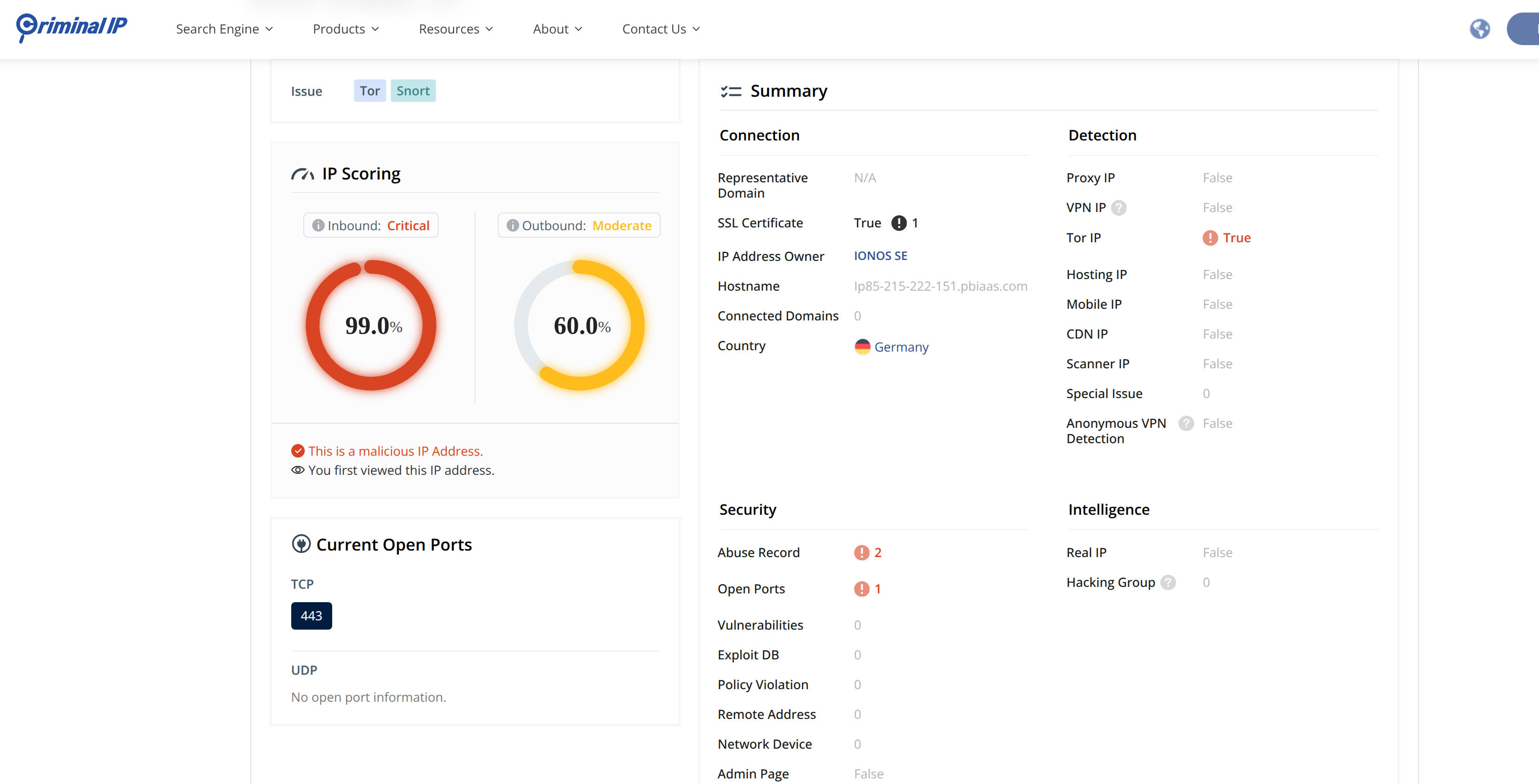
The risk score is the first, immediate red flag. A low score for an admin login is already highly suspicious. But Criminal IP goes further, providing contextual tags like is_tor, is_proxy, or is_vpn.
A low score or a `is_tor` tag isn’t just a risk; it’s a confirmed attempt to anonymize a privileged action.
This combination of score and context gave us the definitive intelligence needed to act.

Phase 2: The “Intelligent” Control (PHP Prevention)
Real-time security needed to happen at the application layer. No network device could react fast enough or with enough nuance. So we went straight into the PHP login flow.
The logic was brutally effective:
- User submits admin credentials.
- System checks: Are the username and password correct?
- BEFORE granting access, the system makes a single, fast API call to Criminal IP with the user’s IP.
- Based on the response (both score and tags), it makes a decision.
The IP check doesn’t just rely on a score; it relies on contextual flags. If an IP, despite a seemingly “Low” risk score, carried an anonymity flag like TOR, admin access was denied.
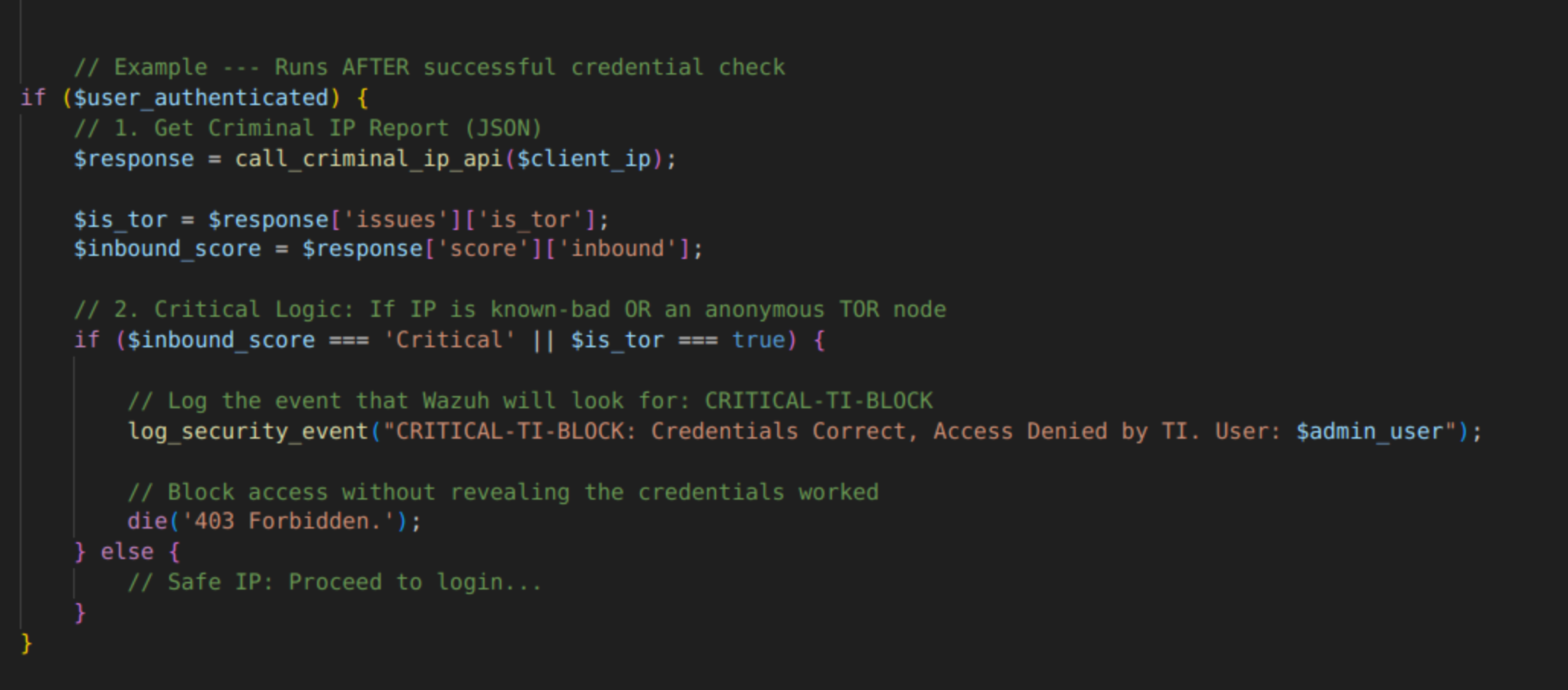
The ideal flow should create two distinct types of blocks, and the difference is everything.
Block A (The Warning): Login failed (wrong password) from a suspicious IP. Okay, just a bot hammering the door. Log it, move on.
Block B (The Critical Hit): Login blocked despite correct credentials because the IP had a critically low score or was flagged as `is_tor`.
This is the moment everything changes.
This isn’t a guess. This is confirmation: someone has a valid password and is actively trying to breach the system from a high-risk, anonymous location.
Phase 3: The Luxury of Tracking (Wazuh)
Blocking the attack is the first priority. But knowing it happened (and knowing it was a real attempt) is what lets you sleep at night.
This is where Wazuh came in. It wasn’t the bouncer; it was the forensic team and the alarm system rolled into one. We integrated it after the fact to handle the fallout from Block B events.
We created a custom, high-priority rule in Wazuh that did one thing: it listened for the specific log entry generated by a Block B event. It ignored all other noise.
When that rule was triggered, it wasn’t just another alert. It was a Level 12 Critical incident fired straight to the SOC team.
The message was crystal clear:
“We have a confirmed compromised credential. An attacker with the right key just tried to pick the lock from a dark alley. This needs immediate investigation.”
It turned a simple “access denied” message into a full-blown identity compromise incident.

this is an example of a CriminalIP and Wazuh integration. source: https://wazuh.com/blog/enhancing-threat-intelligence-with-wazuh-and-criminal-ip-integration/
Conclusion: The Lesson Learned
Security isn’t about building higher walls. It’s about building smarter gates.
We didn’t screw over the end-users who needed their VPNs. We let them work in peace. But for the one place that could cause a catastrophe, the admin panel, we intervened.
The success wasn’t just in blocking Tor or low-level VPN. It was in understanding that some IPs are a massive risk factor for privileged access. It’s about giving weight to intelligence.
Sometimes, the most critical security fix isn’t a complex algorithm. It’s just basic common sense, powered by the right data, applied exactly where it hurts the most.